- Published on
Android CTF Juicy Bar::Code Obfuscation
- Authors

- Name
- Ajin Deepak
Welcome all,
I wanted to do a quick writeup series on the android ctf application called juicy bar. If you haven't tried it out yet please check it out. It's really nice and beginner friendly.
I will try to cover most of the challenges, but this will be very random. I won't be following any particular order. Okay, let's get on with the challenge already.
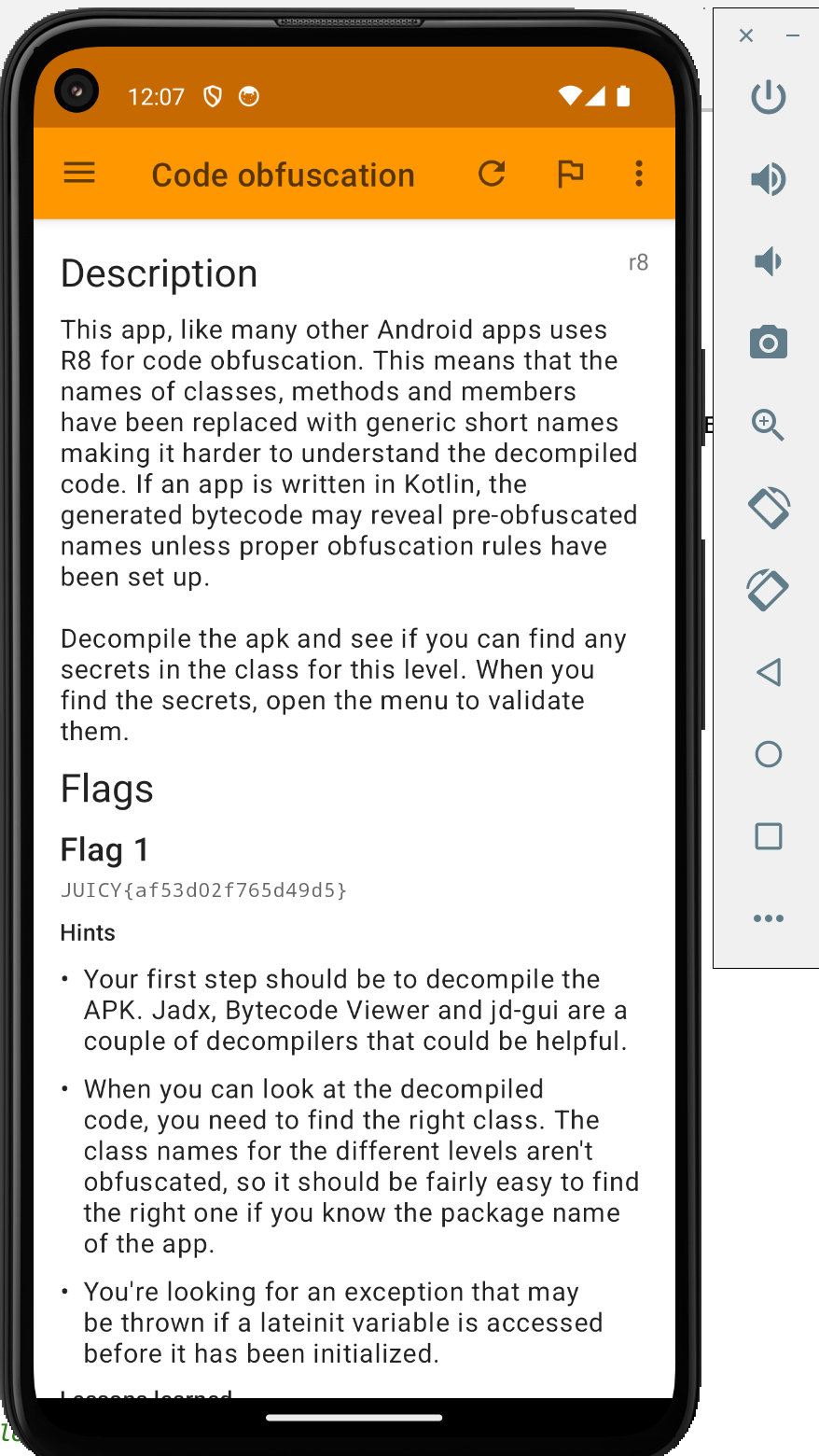
We need two flags to complete this challenge. If you look at the hints, it says to use Jadx and look for an exception that may be thrown for a lateinit variable. Let's load the APK in the JADX.
Flag One
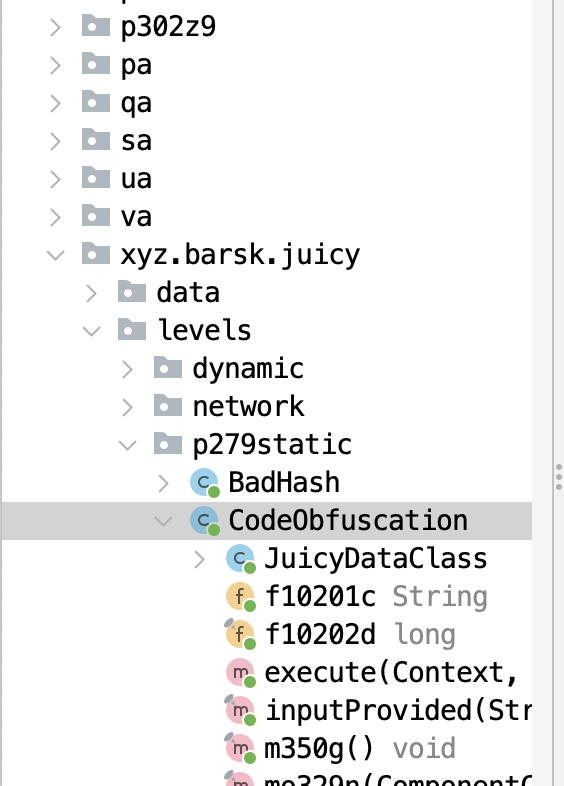
This is the responsible class for this challenge. So let's examine the code based on the hints we got. Let's search for "throw".
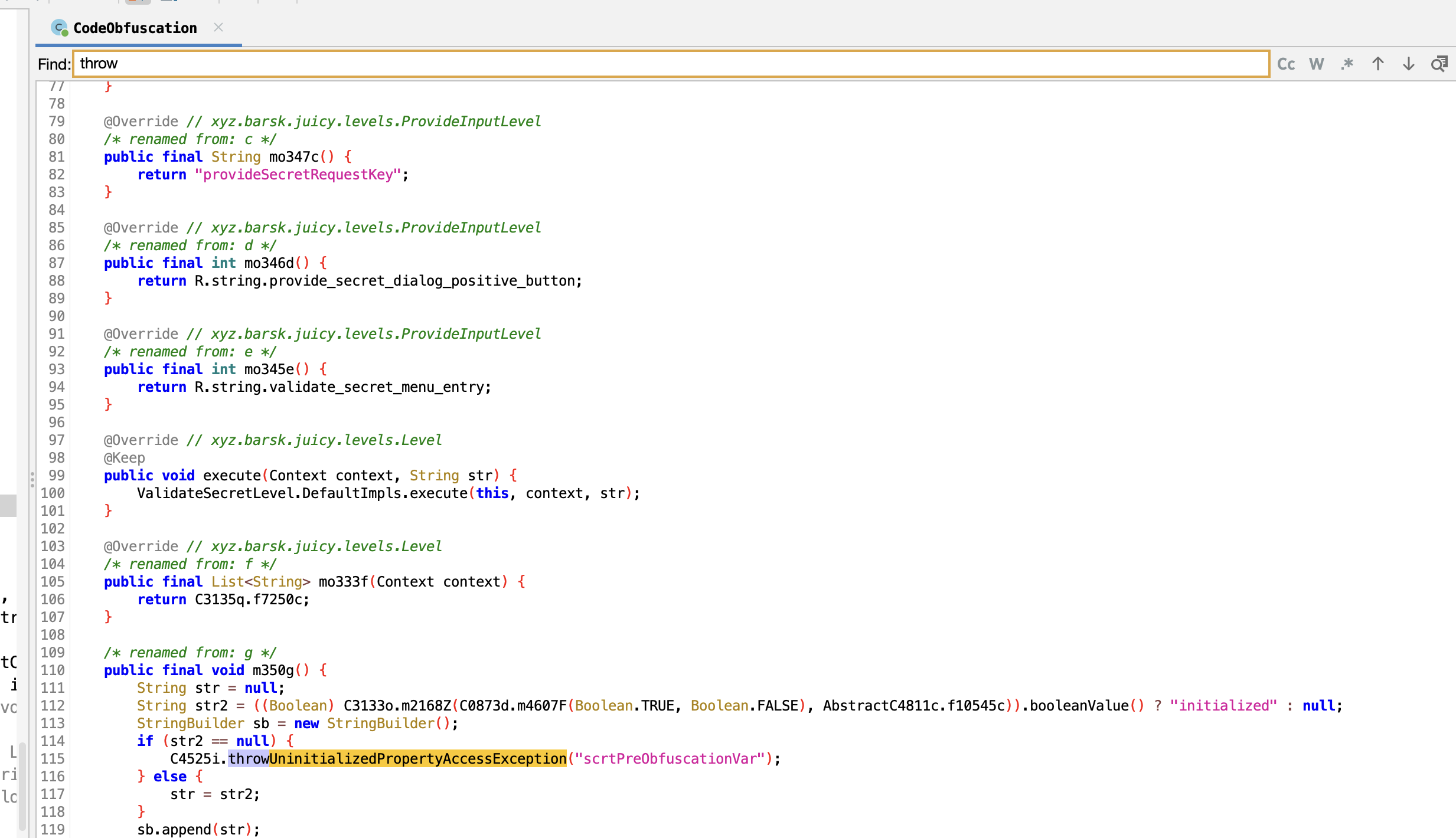
Okay we got something. Let's try pasting that string "scrtPreObfuscationVar".
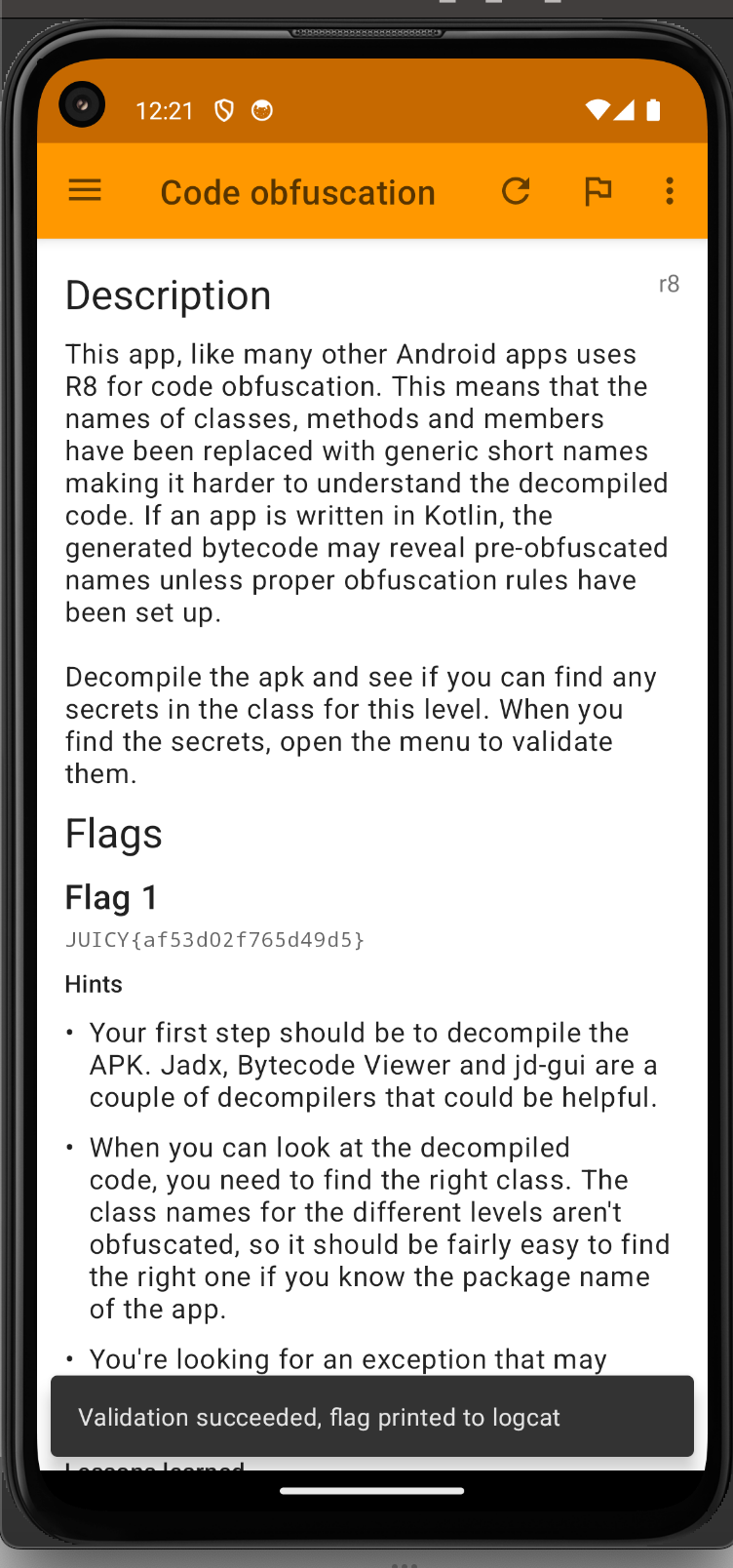
If you check the Logcat now, you should have received the flag. Okay now let's check the hints for the second flag.
Flag Two
Let's check for the toString() method.
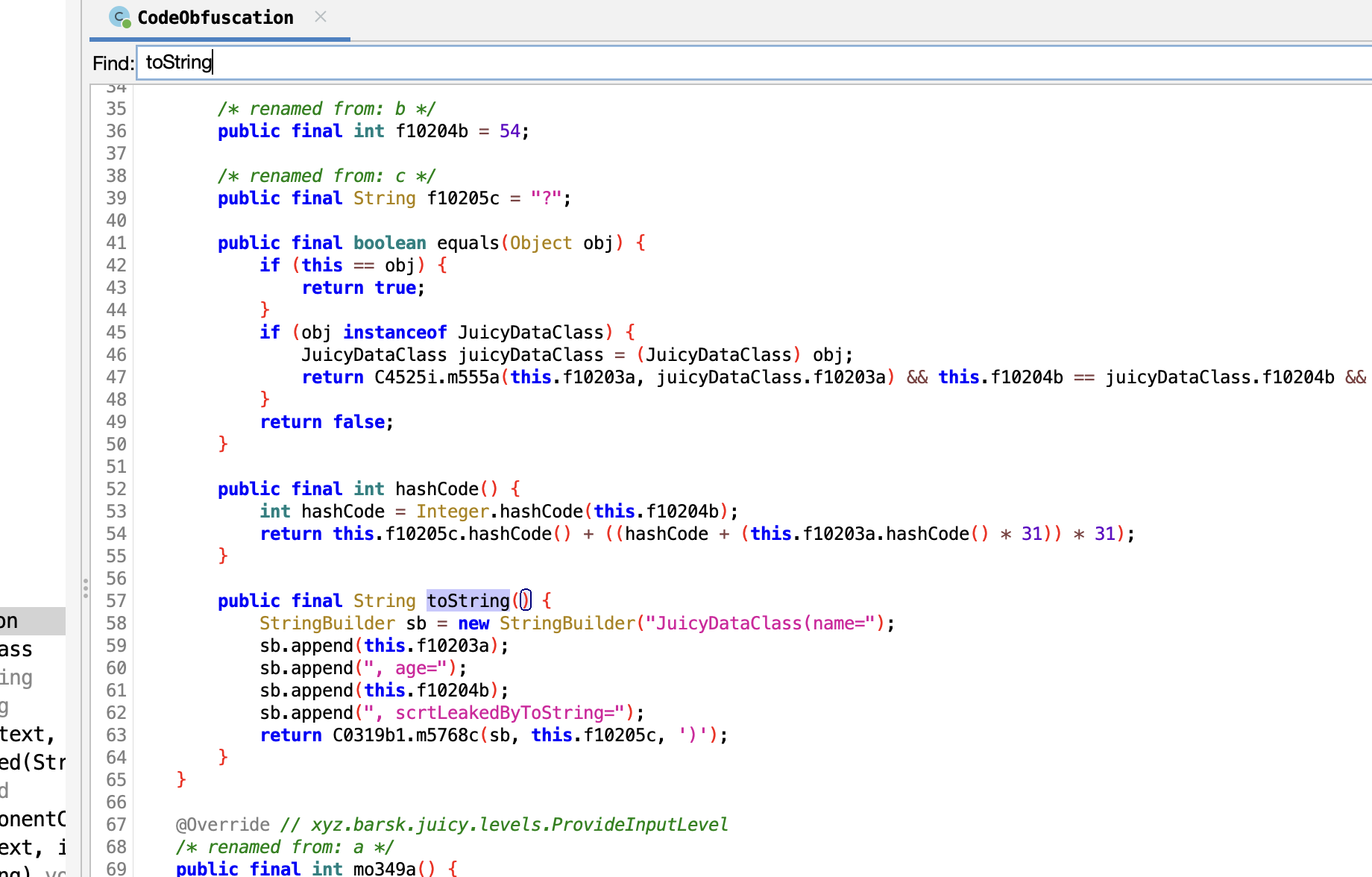
Hmmm. This string "scrtLeakedByToString" looks interesting let's try that.
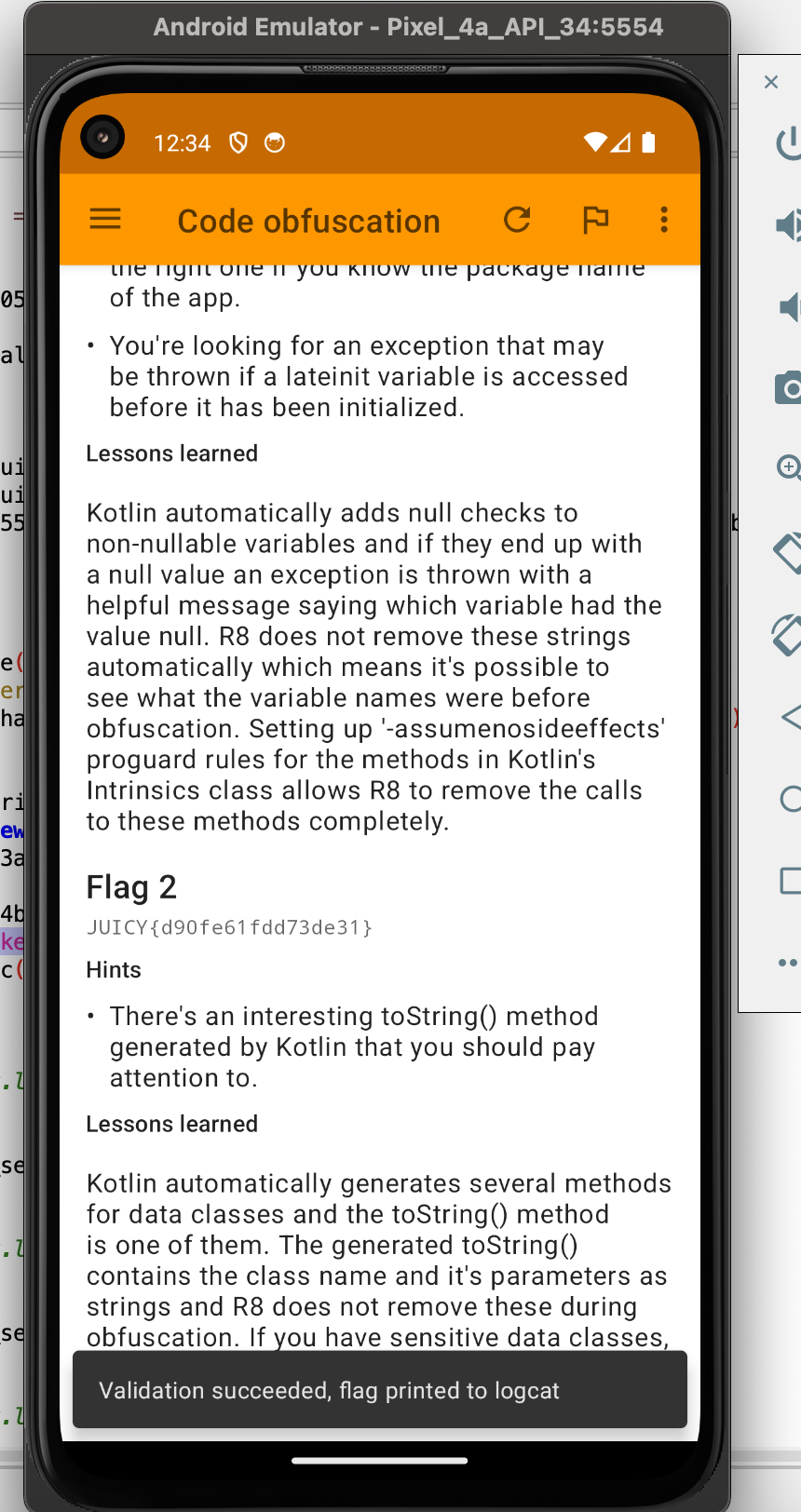
Yes!! We got the second flag. The challenge is now completed.