- Published on
Android CTF Juicy Bar::Hardcoded Secrets
- Authors

- Name
- Ajin Deepak
Hey all,
Let's continue with the walkthrough of the juicy bar CTF Application.
Challenge
Today we will be solving the Hardcoded secrets challenge. We have to find three flags to complete this challenge. Let's start with the first flag.
Flag One

The hint says to look for the api keys in the resources.
Most of these string values including keys will be defined in the string resource file. Let's take a look there.
Now let's search for api.
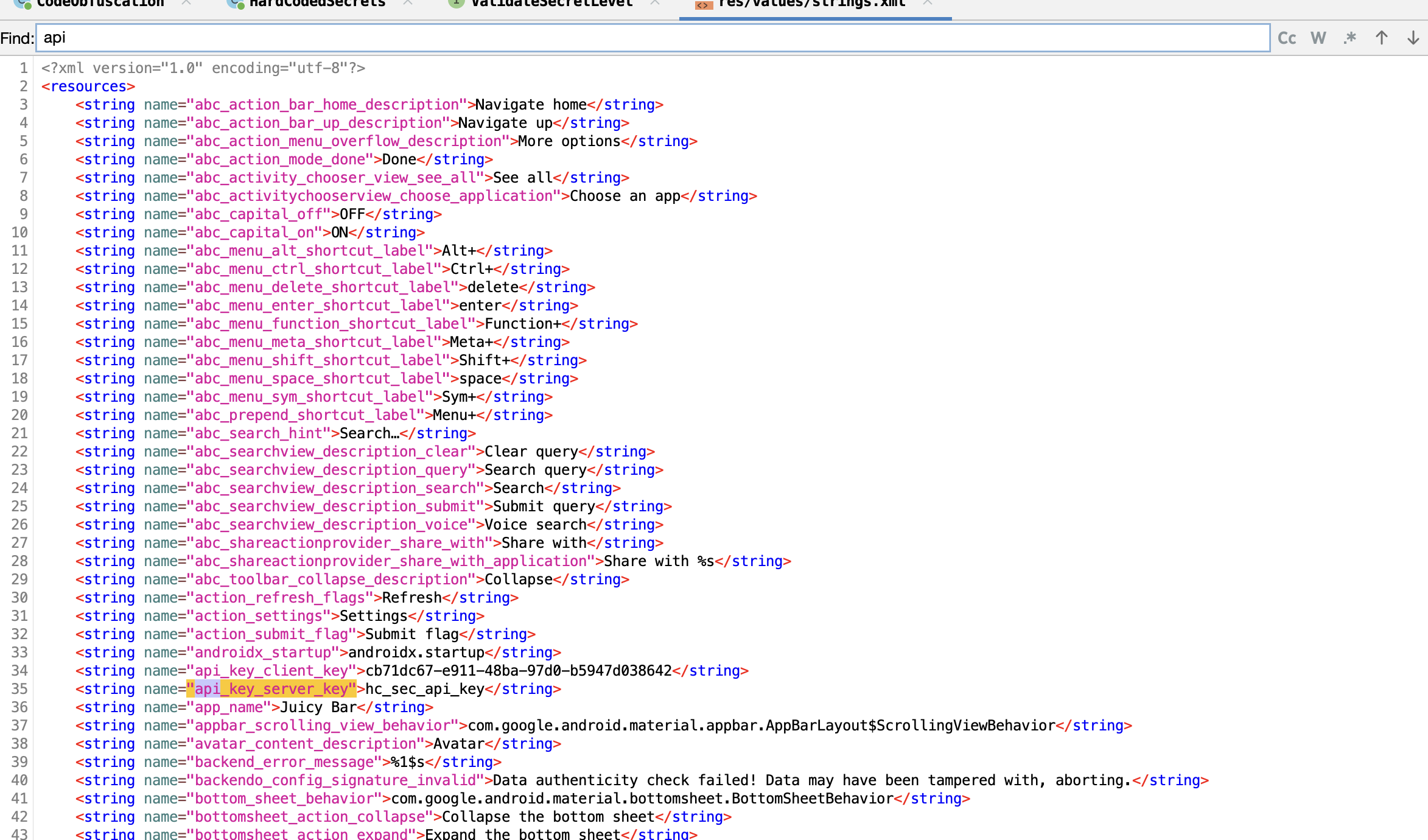
Let's try validing the value for the api_key_server_key.
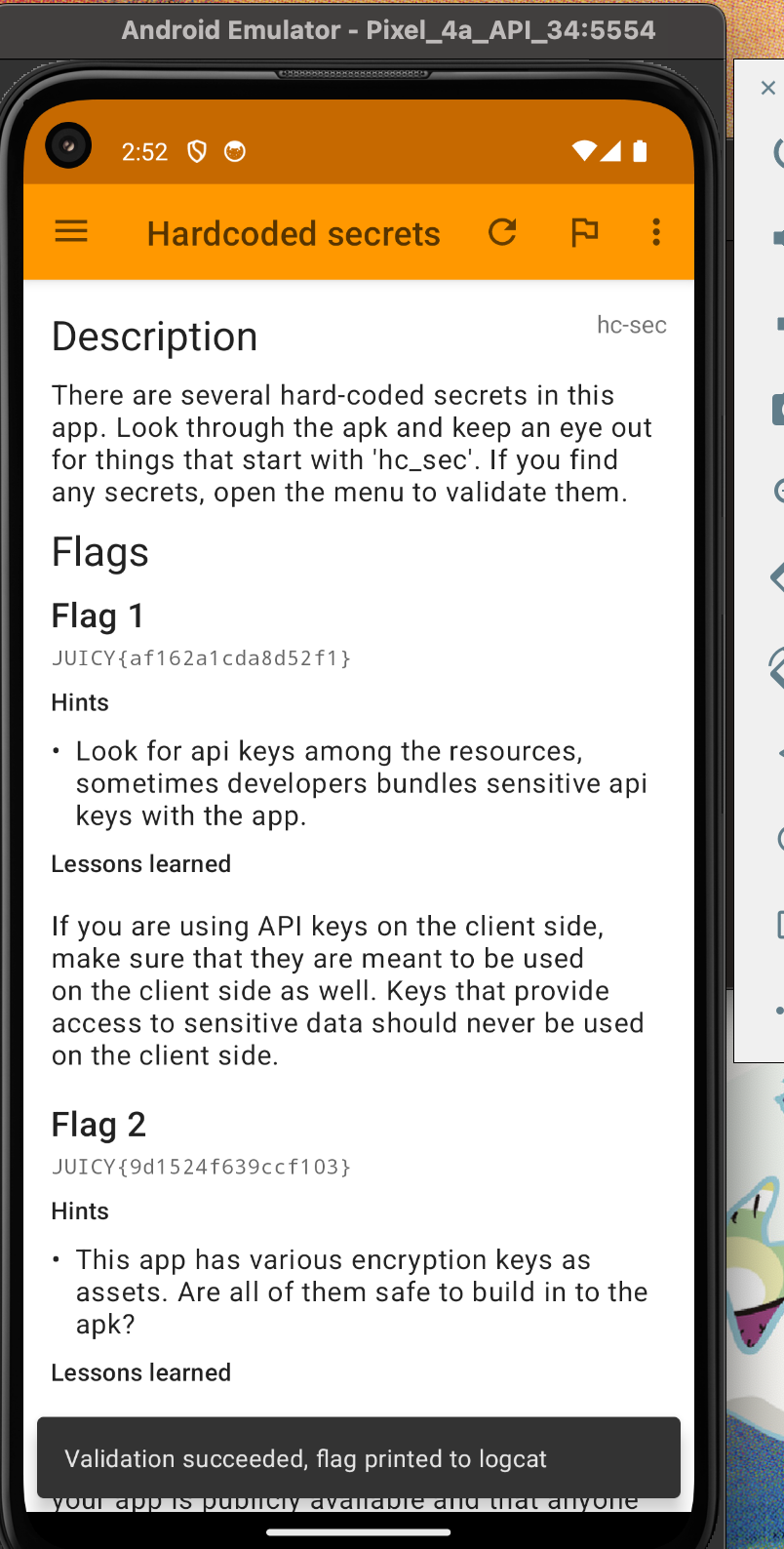
If you check the logcat you should have received the first flag. Now let's first the second flag.
Flag Two
Let's check the hints.
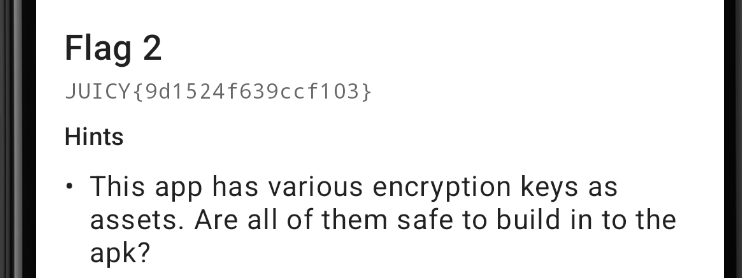
The hint says to look for an encryption key in the assets folder. Let's do that.
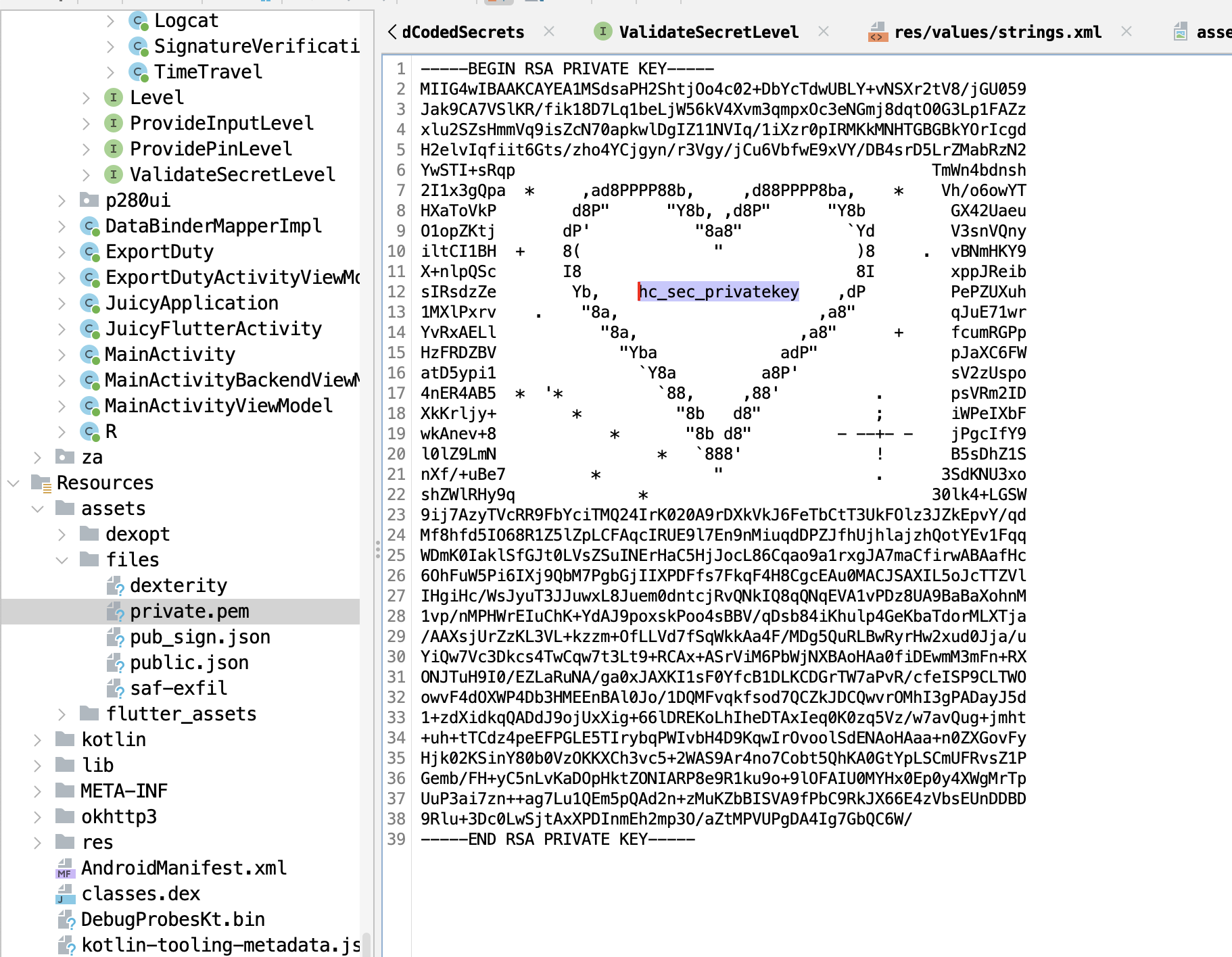
If you go through the folders in the assets , you will easily get the key. Let's try that.
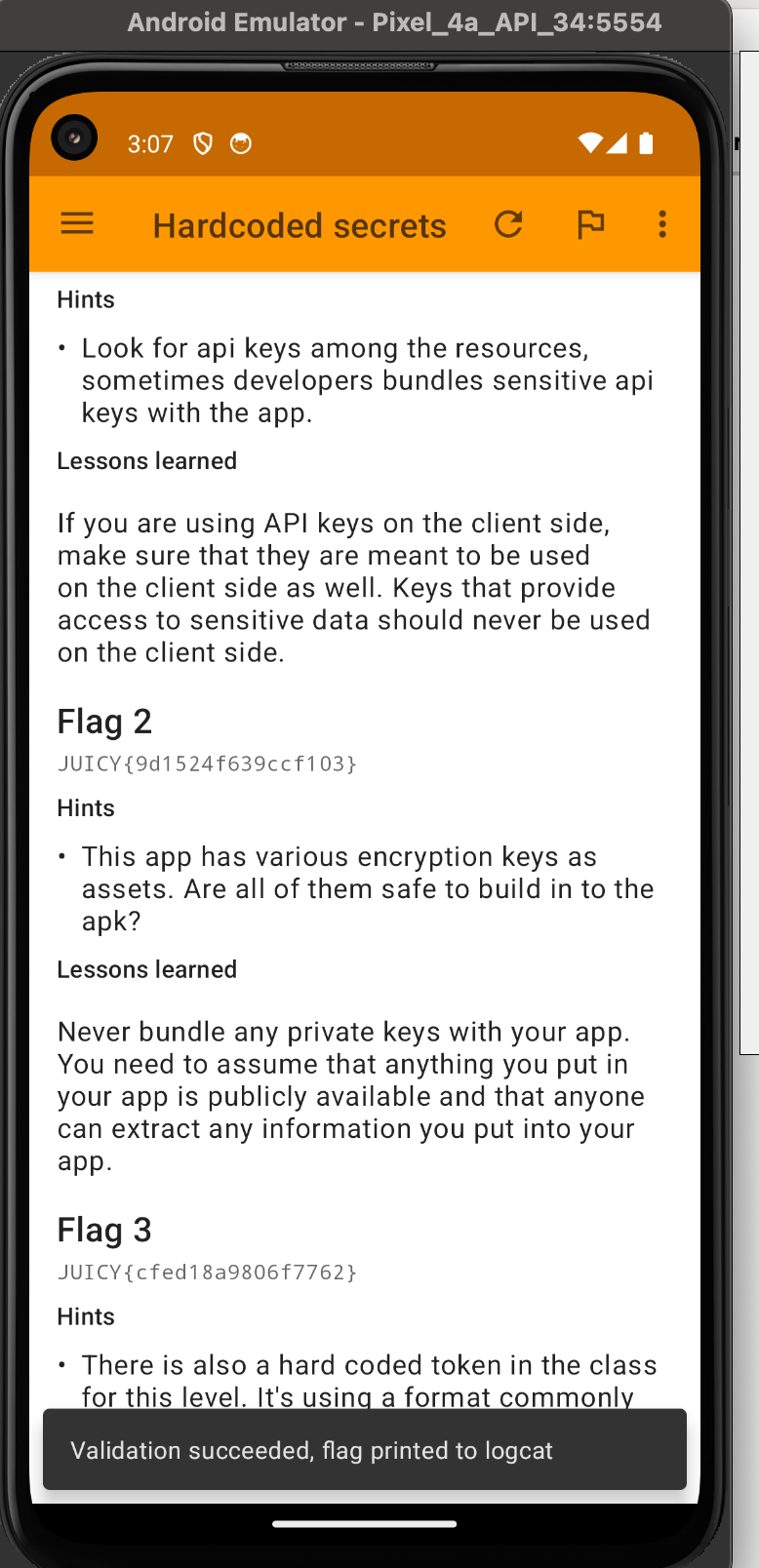
Okay we got the second flag now. Let's complete this thing by finding the third flag.
Flag Three
Let's check for the hints again.
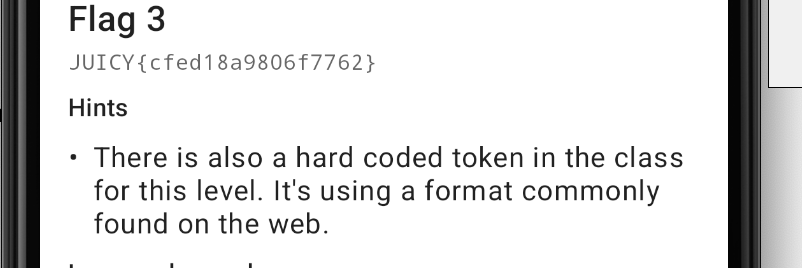
The hint suggests it's a token commonly used in web applications, probably a JWT token. Let's examine the decompiled code in the HardcodedSecrets class.
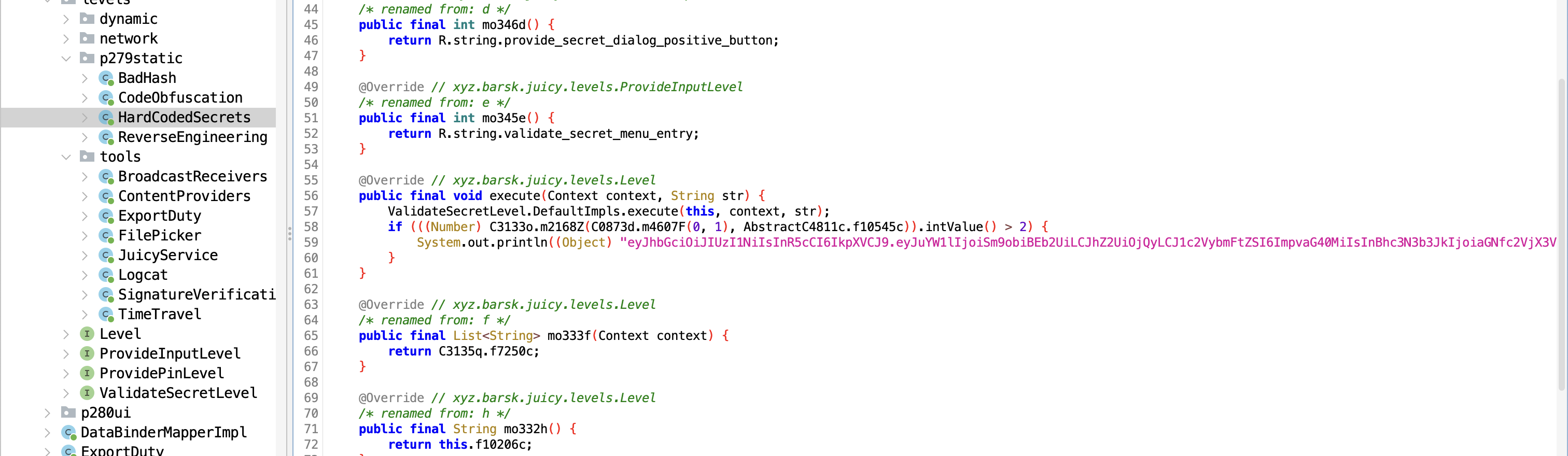
This indeed looks like a jwt token.
System.out.println((Object) "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiSm9obiBEb2UiLCJhZ2UiOjQyLCJ1c2VybmFtZSI6ImpvaG40MiIsInBhc3N3b3JkIjoiaGNfc2VjX3Vuc2FmZV9qd3QifQ.ym7jNSXpVEO5c07lLzp-hlgqm5YRuGtHZrODr4rnayI");
Let's paste this into https://jwt.io/
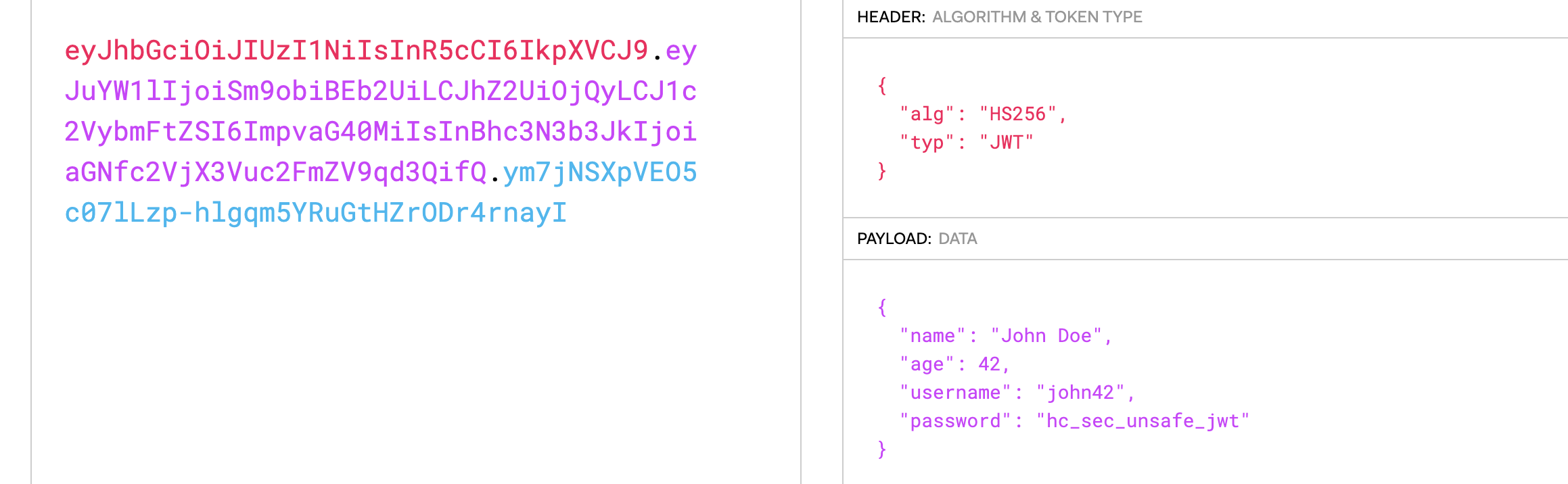
So the secret is 'hc_sec_unsafe_jwt'. Let's try validating this in our app.
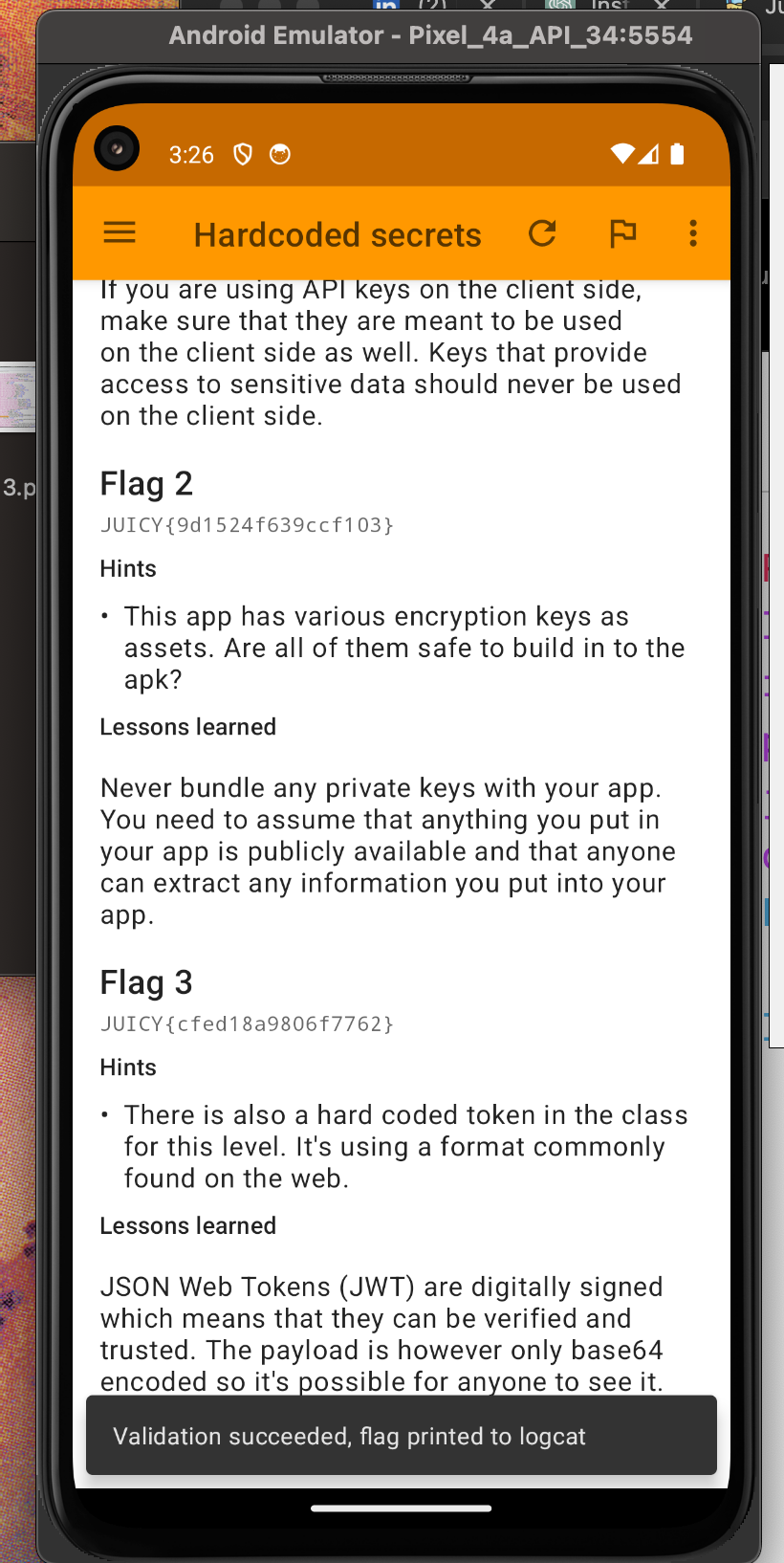
Yay we got final flag. So we have completed the hardcoded secrets challenge. Congrats :)